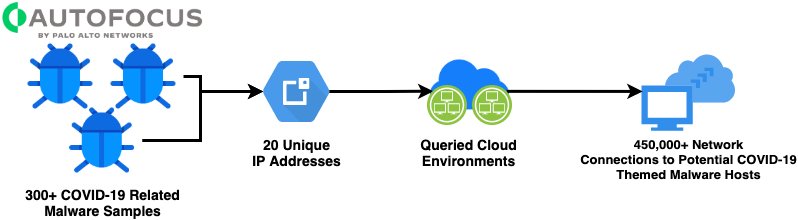
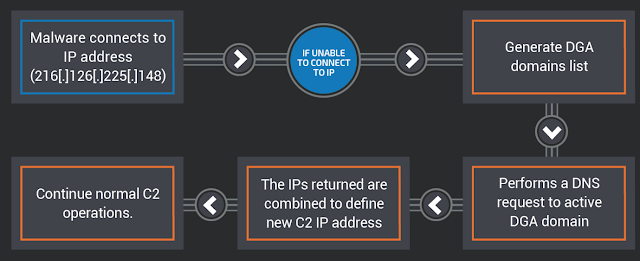
MalwareHunterTeam on Twitter: "TIL about some very malicious IP addresses thanks to Comodo and CMC: 127.0.0.1 8.8.8.8 1.1.1.1 192.168.0.1 Block them all!!! 😂 https://t.co/93P5S45FdS" / Twitter

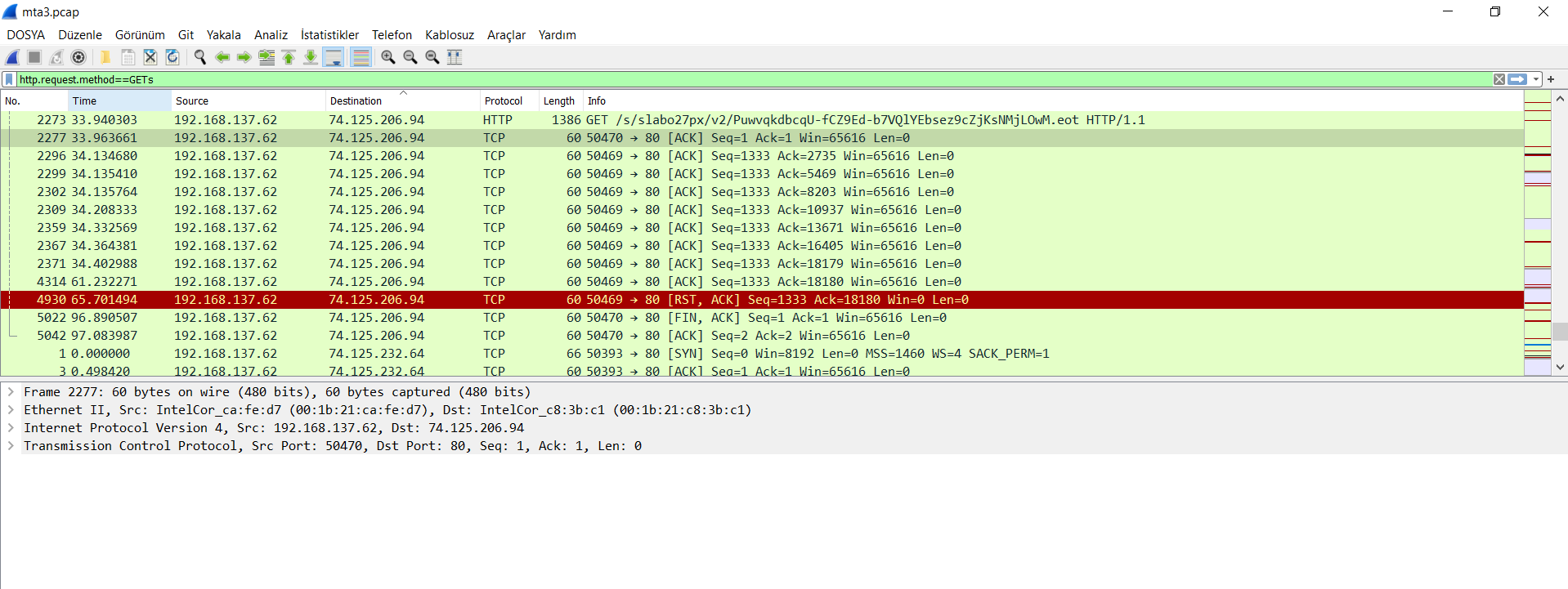
Any way to check/list the IP addresses in ThreatRadar - Malicious IP database | Imperva Cyber Community

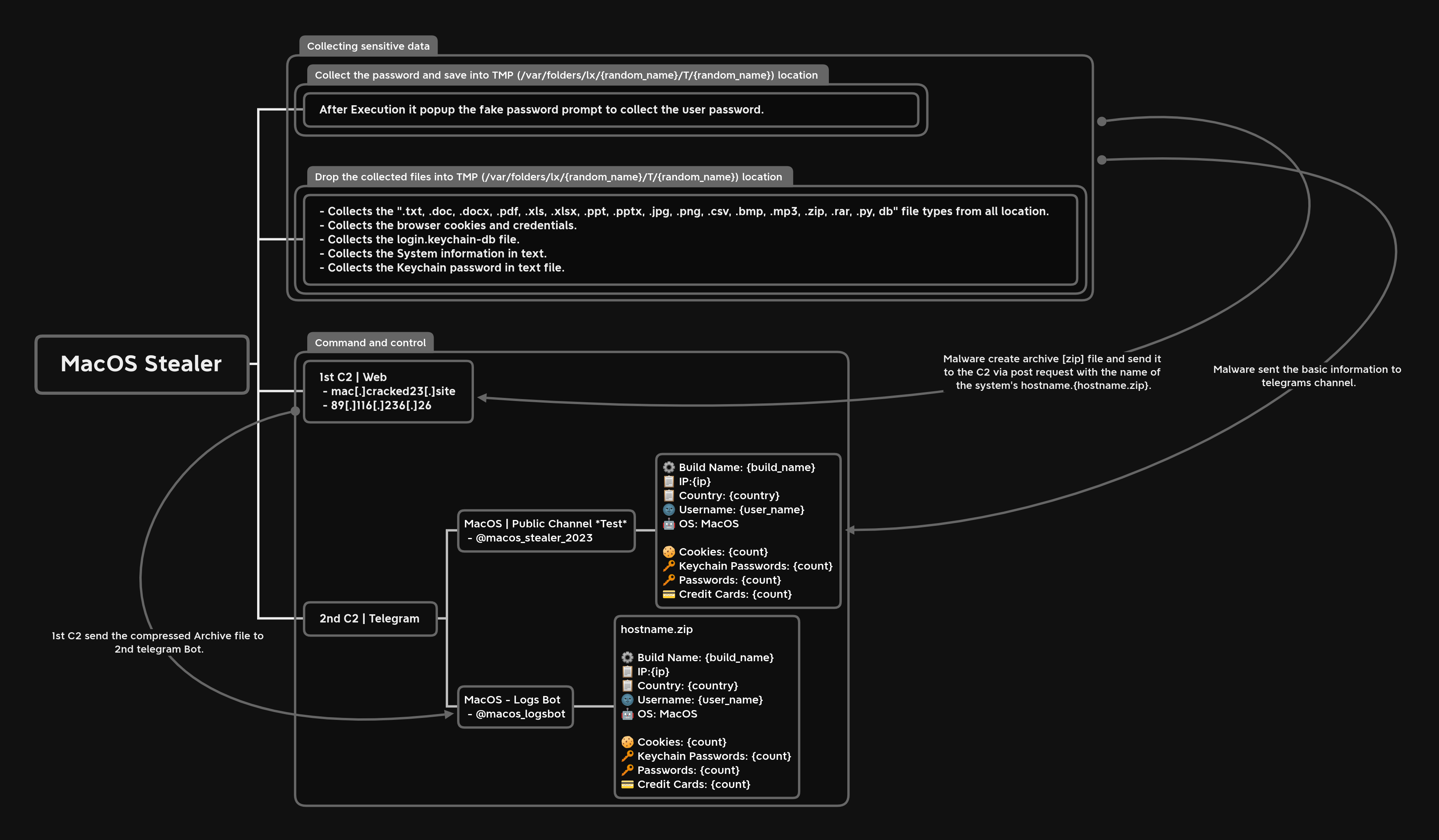
Intelligent Dynamic Malware Detection using Machine Learning in IP Reputation for Forensics Data Analytics - ScienceDirect
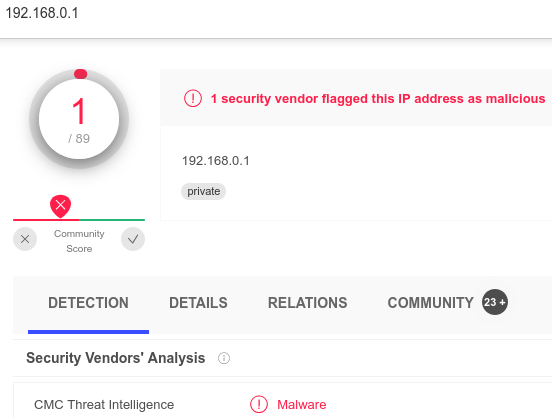
MalwareHunterTeam on Twitter: "TIL about some very malicious IP addresses thanks to Comodo and CMC: 127.0.0.1 8.8.8.8 1.1.1.1 192.168.0.1 Block them all!!! 😂 https://t.co/93P5S45FdS" / Twitter





![5 Ways to Report an IP Address [2023 Guide] 5 Ways to Report an IP Address [2023 Guide]](https://whatsoftware.com/wp-content/uploads/2016/03/multirbl.png)


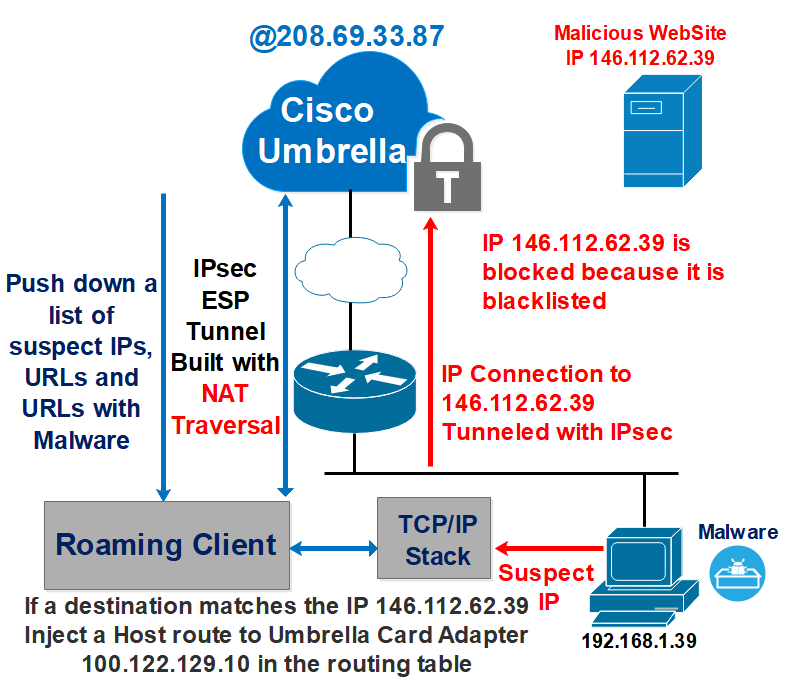
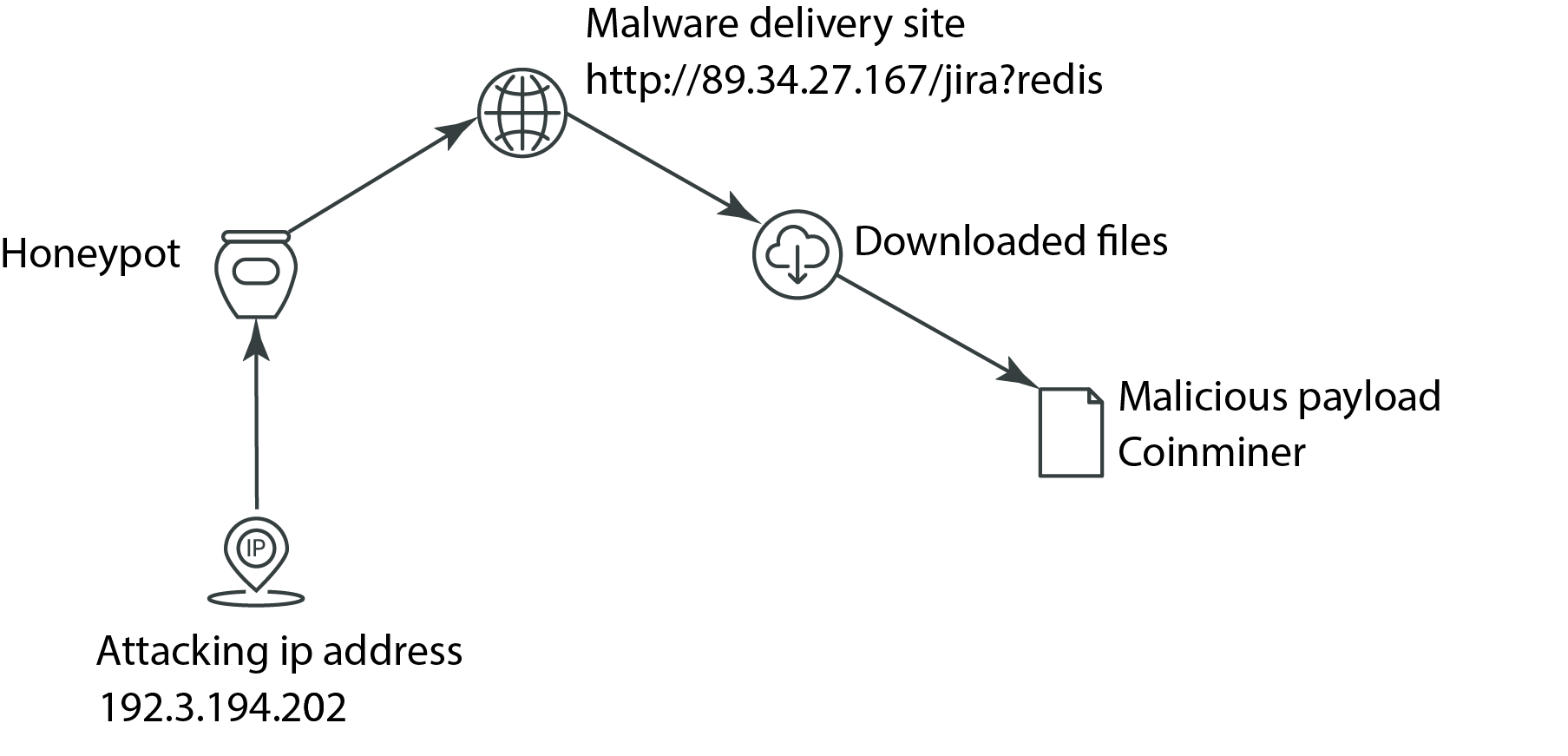
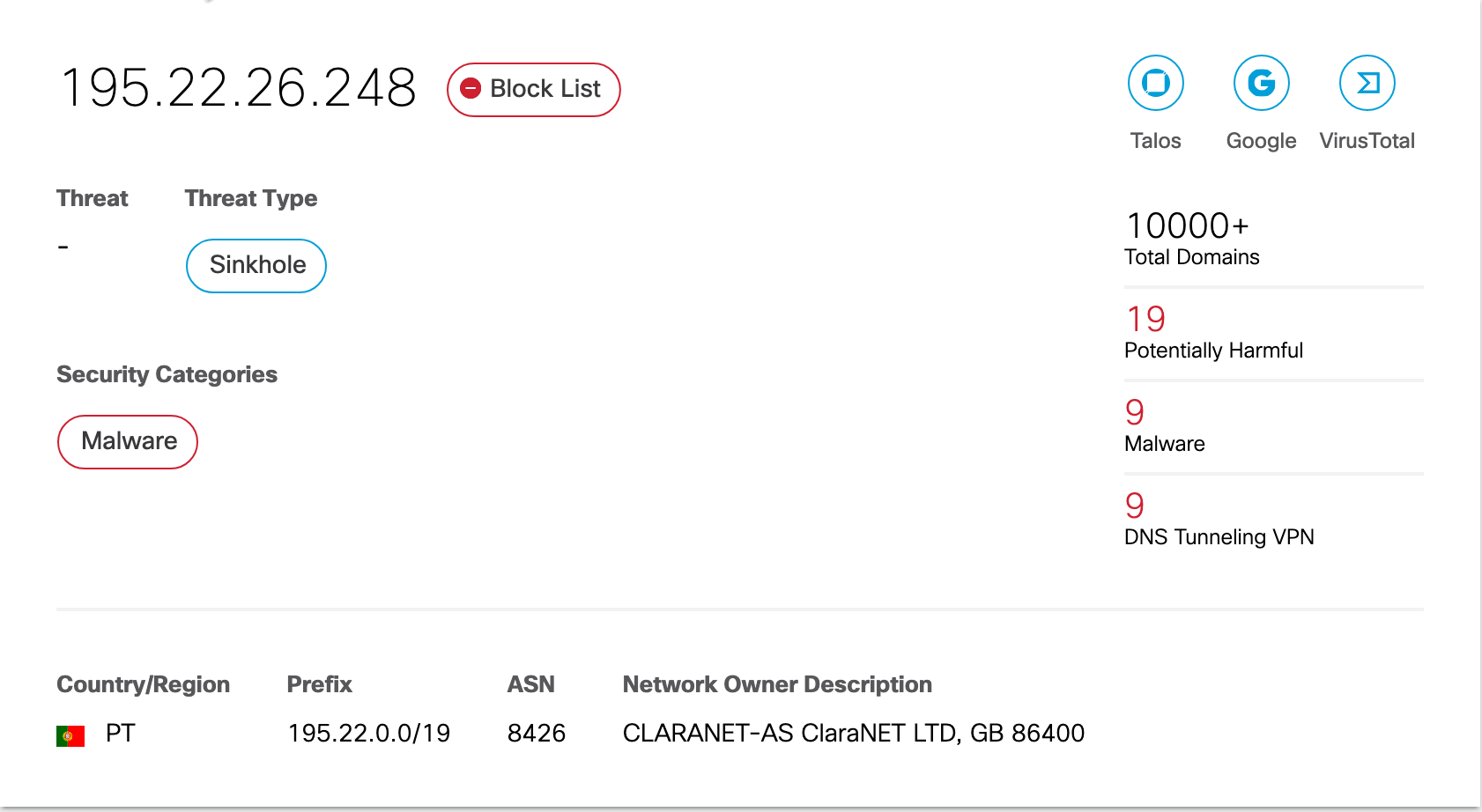
![Malware download sources (IP addresses)[9]. | Download Scientific Diagram Malware download sources (IP addresses)[9]. | Download Scientific Diagram](https://www.researchgate.net/publication/340311707/figure/fig8/AS:876543383453697@1585995636130/Malware-download-sources-IP-addresses9.png)